News:
(20 September 2006) Featured in Forbes. (Section "'Interesting' attachments")
Neat Stuff
People are drawn in by websites containing fun content or something humorous, and they generally want to share it with their friends. In turn, the peoples' friends generally enjoy the site and will often share it with their friends too. This is considered social transmission: referral to a location based on reccommendation of peers.
Many websites, including Carlton Beer's www.bigad.com.au use Java Applets (Java programs embedded in web pages) to display content. A Trusted Applet is given more access on the visitor's computer in order to display full-screen video or make network connections.
People's willingness to trust their friends (and general lack of understanding about signed applets) lead to a possibility that the signed applets are installing viruses or other malware on visitors' computers.
Technology
Trusted Applets essentially have no restrictions. An applet is considered trusted when the following conditions are met:
- The code (usually a JAR file - a java archive containing the code) has been signed by the author).
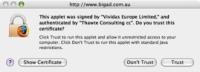
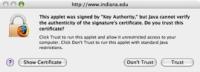
- The browser has verified the signature against a certificate provided by the applet's author
- The client's browser accepts the certificate as trusted: it is issued by a trusted authority such as Thawte or Verisign and accepted by the user, or the user (who is prompted) chooses to accept an un-trusted certificate. The most common un-trusted certificate is not signed by an authority at all, but self-signed: the person who created the application also signs the certificate to say the applet should be trusted.
Before an applet is loaded, it is verified using the provided certificate and then the browser displays a "do you wish to run this applet" prompt to the user (see sidebar). If the user clicks "Yes", then the applet is trusted and given heightened access to the visitor's computer. Many people will click "Yes" without reading the prompt.
Vulnerability
We have found that at people will quickly grant applets unrestricted access to their computers when they think a website should be trusted for one of many reasons including: friends recommending the website or the site appears (though is not proven) to be authored by a socially-accepted group or company. An attacker can masquerade as this group or peoples' friends in order to get visitors to allow malicious code to be installed onto their machine.
Once its Applet is authorized, the Carlton Beer site downloads and installs the Vividas media player onto a visitor's computer. This application is then run to provide access to streaming media that is presented in full screen. The result is a video that starts to play immediately.
The ability to download and install arbitrary executables onto a computer would allow an evil person to install malware instead of a media player. An even more malicious person could do both, thus making it seem like all that was run was a media player when in fact other software was installed in the background
A clever attacker could mirror the site and draw people to his site instead. He would erect a site that appears exactly the same but the applets would be re-packaged and re-signed to contain the malware too.
Our experiment
In an attempt to assess how successful such a mirror attack could be (where existing applets were injected with malware), we erected an exact copy of the Carlton Beer site at http://www.verybigad.com by downloading all the files from their server and placing them on ours.
To simulate an attacker's site, we then deleted the certificates and removed signatures from the Applets and created our own self-signed certificates. We did not change the code in the applets to include malware, but we could have at this point.
Next, we modified the website to record each visitor's access when (1) they initially loaded the site, (2) when they loaded the quicktime copy of the video that was not deployed by a signed applet, and (3) when the visitor finished loading the signed applet. This allowed us to gauge what percentage of visitors clicked "yes" to run the possibly malicious self-signed applet.
We found that roughly 70% of the visitors to the site loaded the self-signed applet. We believe this to be a low estimate, due to some difficulties we encountered in deploying the site; clients with some versions of Internet Explorer were not properly delivered the applet, so they could not run it. This added to the number of hits to the site that did not load the applet (though perhaps they wanted to).
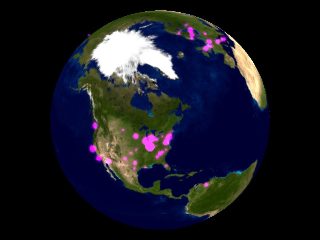
Social propagation
It was interesting to see from where the hits to our website originated. We created a time-lapse visualization of all the visitors to the site. Click on the image below to view the video of visitors. We are currently working on a visualization that differentiates between visitors who accepted the self-signed applet and those who did not.