
 |
Phishing Projects
Using Cartoons to Teach Internet Security  While good user education can hardly secure a system,
we believe that poor user education
can put it at serious risk. The current problem of online
fraud is exasperated by the fact that
most users make security decisions, such as whether to
install a given piece of software or not,
based on a very rudimentary understanding of risk. We have
developed a cartoon approach aimed at teaching
Internet security to typical computer users. We believe
that our approach has benefits compared to currently
practiced
educational efforts with the same general goals, based on
our four design criteria: (1) A research driven
content selection, according to which we select educational
messages based on user studies;
(2) accessibility of the material, to reach and maintain a
large readership; (3) user immersion in the
material, based on repetitions on a theme; and (4)
adaptability to a changing threat.
[ web page ]
[ paper ]
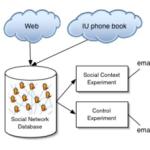
Social Phishing    The fundamental purpose of this study was to
study the effects of more advanced techniques in phishing using
context. Receiving a message from a friend (or corroborated by
friends), we hypothesized the credibility of the phishing attempt
would be greater.
[ blog ]
[ slides ]
[ CACM preprint ]
[ More Information ]

Browser Recon and Countermeasures  One can use a simple technique used to
examine the web browser history of an unsuspecting web site visitor
using Cascading Style Sheets. Phishers typically send massive
amounts of bulk email hoping their lure will be successful. Given
greater context, such lures can be more effectively tailored---perhaps
even in a context aware phishing attack.
[ blog ]
[ paper (pdf) ]
[ More Information ]
Socially Transmitted Malware   People are drawn in by websites containing
fun content or something humorous, and they generally want to share it
with their friends. This is considered social transmission: referral
to a location based on reccommendation of peers. We measured possible
malware spread using social transmission.
[ More Information ]
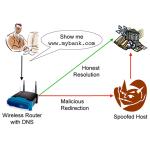
Phishing with Consumer Electronics: Malicious Home Routers It is easy to "doctor" a wireless
router like the ones found at home or at a local
WiFi hotspot to misdirect legitimate browser links to phoney
and often harmful websites.
[ workshop paper (pdf) ]
[ More Information ]
Net Trust Individuals are socialized to trust, and trust
is a necessary enabler of e-commerce. The human
element is the core of confidence scams, so any solution must
have this element at its core.
[ workshop paper (pdf) ]
[ slides ]
[ More Information ]
Scammers, such as phishers and purveyors of 419 fraud, are abusing trust on the Internet. All solutions to date, such as centralized trust authorities, have failed. Net Trust is the solution -- trust technologies grounded in human behavior. A Riddle Could your browser release your personal
information without your knowledge?
[ Go to the Riddle ]
|